Allow Ports Through UFW Firewall
Learn how to open ports in Ubuntu and allow selected services through the firewall.

If you are setting up an Ubuntu system that connects to other systems and accepts connections, you need to allow the necessary ports through the firewall.
So this guide is going to utilize the UFW (Uncomplicated Firewall) that comes pre-installed on Ubuntu.
You don't need to have the UFW activated for opening a port or changing any other rules.
Let's say you want to allow port no. 22 which is used for SSH, your command would be:
sudo ufw allow 22/tcp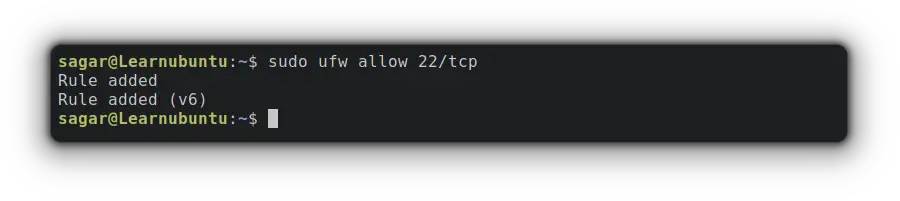
Now, you can check whether the rule was successfully added or not by checking the status of the firewall which also gets the added rules:
sudo ufw status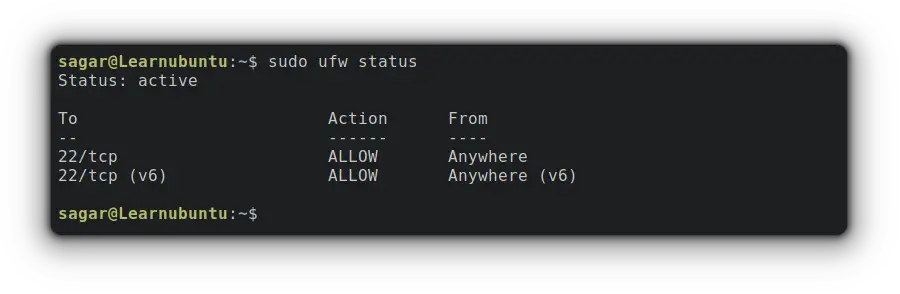
A straightforward process right? And if you want to learn some basics of ports including the most commonly used ports, the given guide will be helpful:
Now let me walk you through adding some useful ports to your system.
1. Allow HTTP (Port no. 80)
To allow HTTP port through the firewall, you'd have to use the given command:
sudo ufw allow http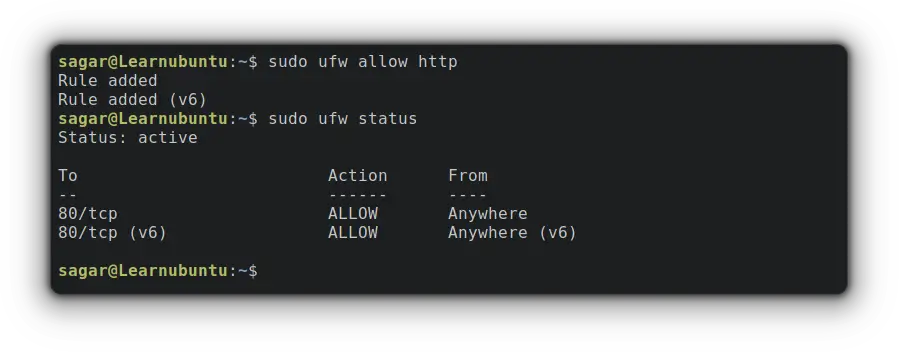
2. Allow HTTPS (Port no. 443)
You can similarly allow HTTPSto what I did in the case of adding HTTP. Let me show you how:
sudo ufw allow https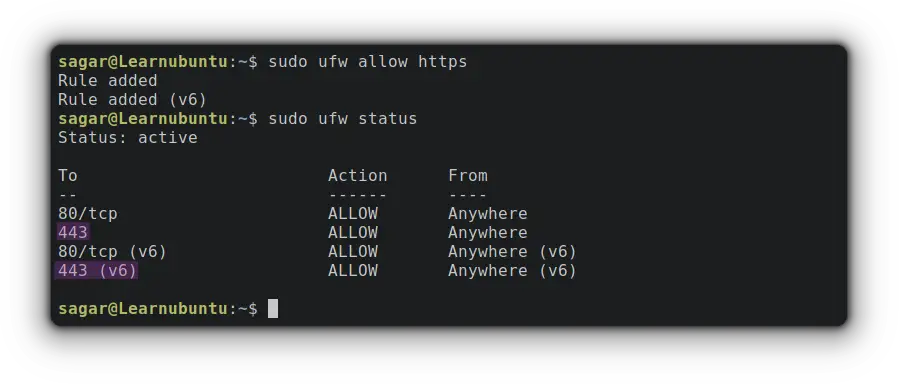

Get started on DigitalOcean with a $100, 60-day credit for new users.
3. Allow HTTP and HTTPS through Subnet
Users can also specify the subnets to accept connections. So let's add HTTP and HTTPS to all IP addresses from 69.171.224.37/16 subnet.
sudo ufw allow from 69.171.224.37/16 port 80,443 proto tcp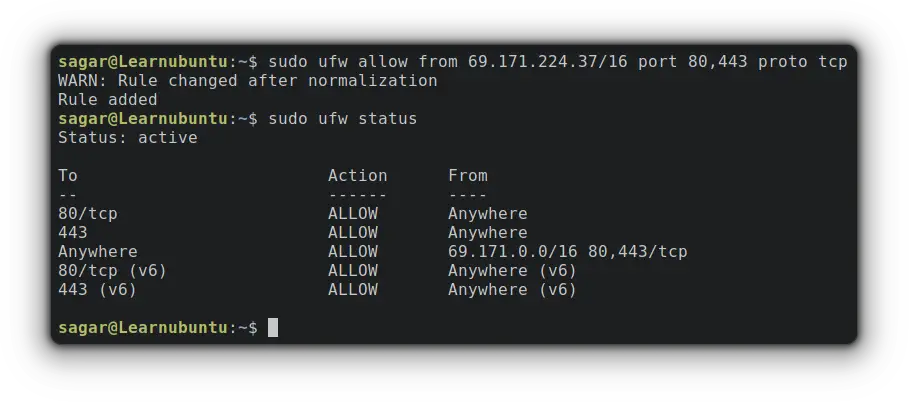
3. Allow SSH from Specific IP
At the beginning of this guide, I explained how to allow SSH through a firewall but you can tweak your firewall to only allow SSH from specific IPs.
So let's suppose I want to allow SSH from 10.0.2.15 so my command would be:
sudo ufw allow from 10.0.2.15 port ssh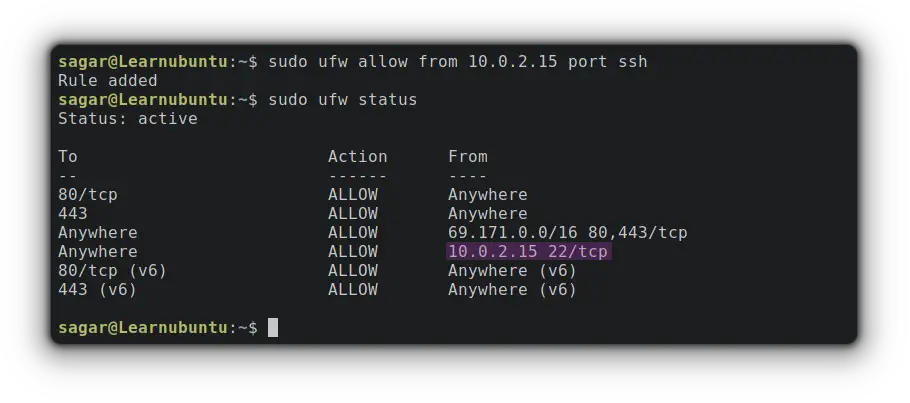
4. Allow Apache through Firewall
It may sound complex but it's the easiest part when configuring an Apache web server. Yep, a single is all you need:
sudo ufw allow "Apache Full"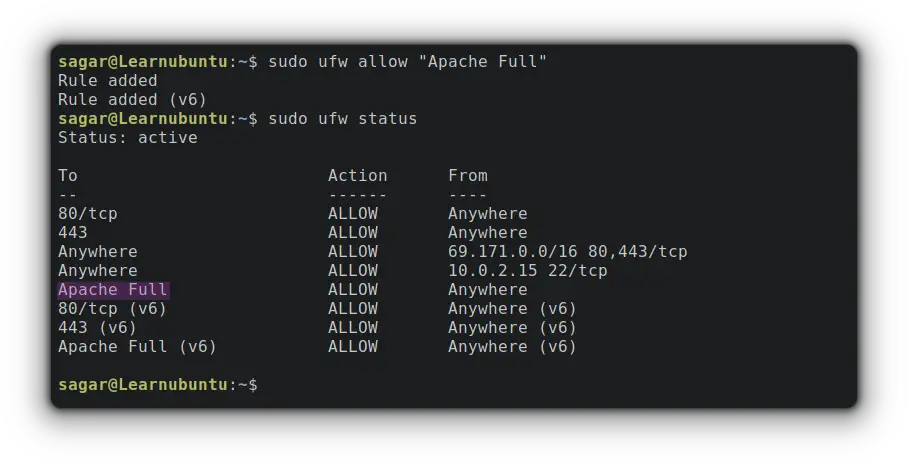
Get started on Linode with a $100, 60-day credit for new users.
5. Allow NGINX through Firewall
This is similar to what I explained just above. Where you're required to use NGINX Full instead of Apache Full. Let me show you how:
sudo ufw allow "NGINX Full"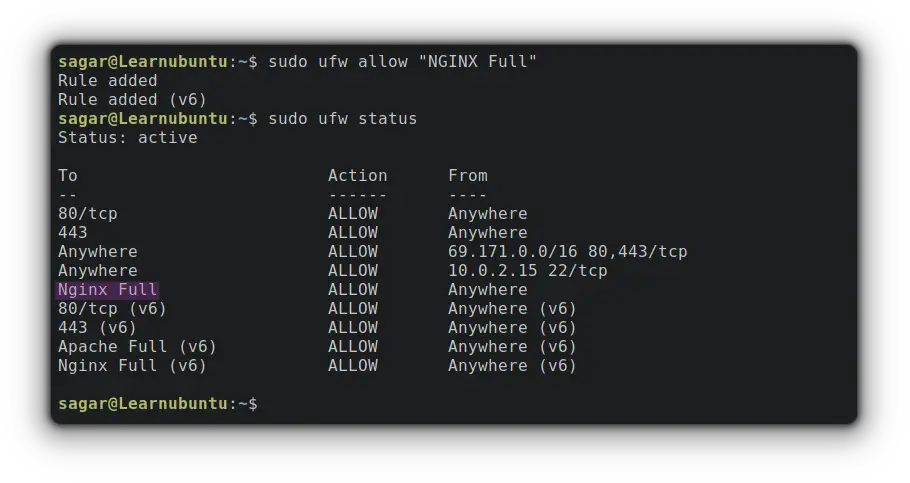
But what about deleting rules that are no longer required? It's quick and easy.
You can always check which ports are open to verify.

How to Delete UFW Rules in Ubuntu
The best way to delete UFW rules is to list them with numbers so we can have a better idea of what to delete and whatnot.
To list UFW rules with numbers, use the given command:
sudo ufw status numbered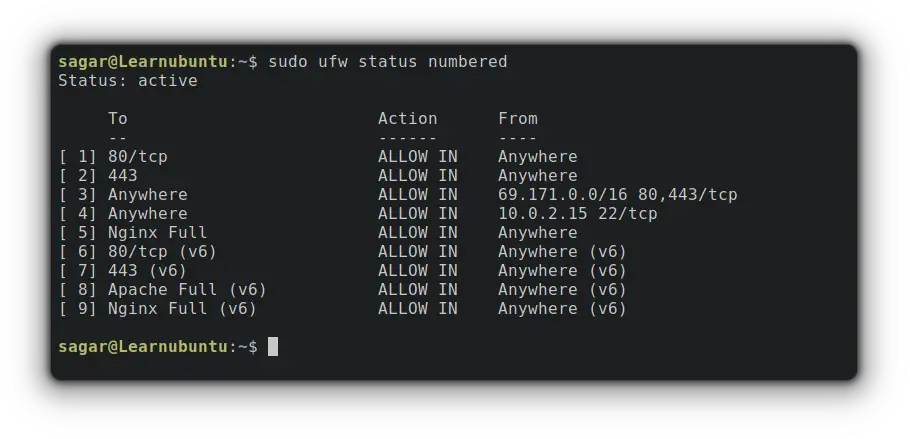
Now, you just have to pick a number of rules. Let's say I want to delete a rule related to Nginx so the associated number with NGINX is 5 so my command would be:
sudo ufw delete 5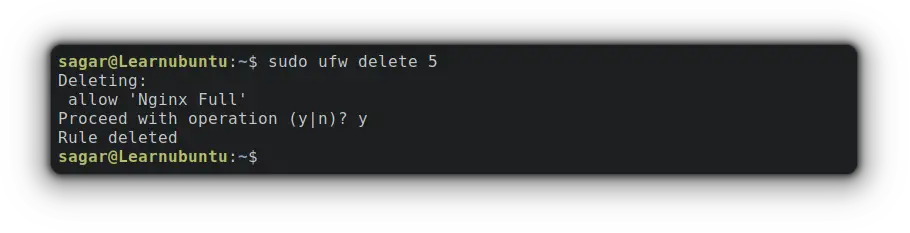
But what if you want to delete each rule?
You just have to use reset option with ufw command as given:
sudo ufw reset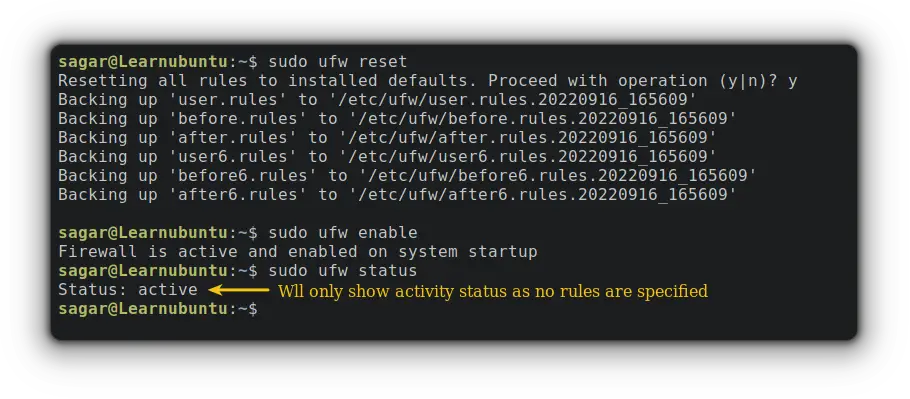
Conclusion
This tutorial explained how you can allow ports with various tweaks to achieve the desired end result, including deleting rules that you no longer require.
And if you have any queries, I'd love to answer them through comments.



